Enterprise network typically has one or multiple branch location and using multiple connections also. When a design and implementing a network need to understand the real requirements of the business to design network to best suit current and future needs.
Most organizations need customer support lines, internal communications lines, and helpful features such as video conferencing. Although traditional telephone lines remain an option, many businesses prefer VoIP solutions that use network connections to transmit voice signals. Dedicated T1 line helps to overcome a range of bandwidth problems to ensure that company has the best possible standard of phone calls. The Quality of Service feature allows you to identify which packets are voice data so that the network gives them higher priority.
Network Architecture
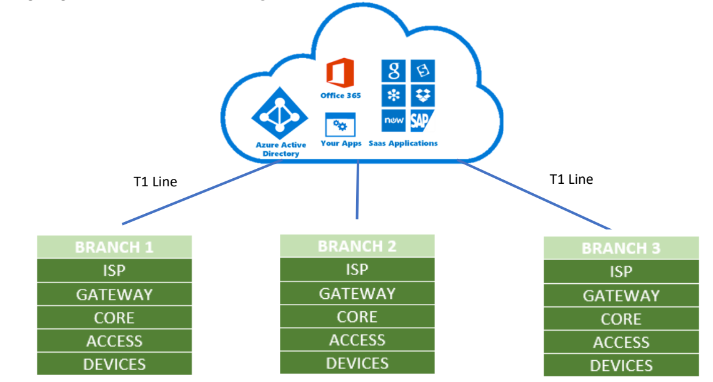
First, we need to select the best ISP service in the region what kind of line is coming. Second Gateway pipe that is going into the network the second branch. Core is our router and we need to pick properly. After Access and then select devices are correct interfaces. Access layer which is either an access switch or in case of Wi-Fi AP and then that interface with the end devices. This is the framework of how we are going to build our network design
Network Scalability
Router on a stick architecture. 8 port POE switch is the center point the core switch and this is a scalable. Because 8 port we can Connect 8 switches or 8 access points
We are dealing with IP Cameras, Servers, Desktop’s, Laptop’s, WIFI AP, Controllers, Switches, Routers, and Some Services Video on Demand, Cloud base solutions, Voice over IP,
Company need to select proper brand and warranty support service to device selection because of high availability. Router we are select Cisco 3640 this router support to Analog T1 Voice network module , channelized T1/ ISDN and E1/ ISDN network modules
Infrastructure Management
The two remote branches connect with the London office through ISP T1 Link
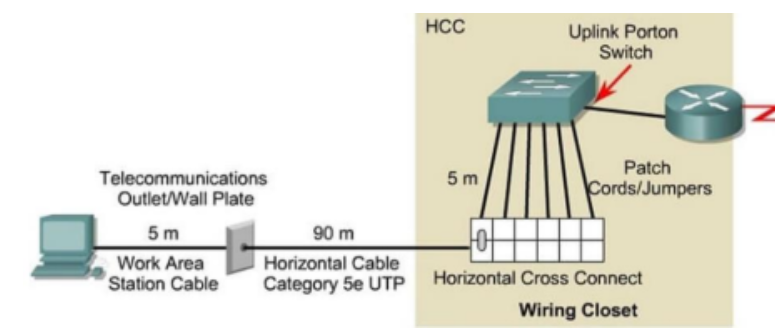
ISP T1 Link stop at the demarcation point and provide an Ethernet link to our router. It connects to the router and router connect to the switch again. All the computers in branch offices has networked using UTP Cat.5e cables. And they connect to the Faceplate from Network card with a 2m patch cord. Then they go to the Telecommunication room through the ceiling or walls from there. After that they connect to the patch panel and switch
Network Overall Topology
After configuration of the network, we divide the appropriate network IP and VLAN’s. Group network security is also extremely necessary. This scenario plan is equipped with a cisco pix firewall and uses the Network Access Control List to fix security issues. This also provides the Redundancy Link and Connection Backup feature.
The overall topology of the benefits of network topology is simpler and more recognizable in terms of complex network structure. Before designing the overall network topology, the group should be examined in detail.
Network Planning
We will split the subnet and use the fair IP address when applying for an IP address.
DHCP assigns the IP address of the client. The server will automatically assign the IP address to the host from the preset pool IP address. DHCP is easily scalable and functional. Deploying DHCP pools for each VLAN on Layer 3 switches automatically enables VLAN access to the address and implements each other’s DHCP backup
VLAN. Logical grouping of devices or users (reduce broadcast domains) Communication between VLANs is via the router. Provides a level of security. When there are two redundant links between Core Switch and Core Router in a branch network. And provides the redundancy required for reliability without creating switching loops
Network security
• Install Microsoft Windows Server Active Directory , AD Federation Service and AD Certificate Service. (AD DS), which stores directory information and manages the interaction of the user with the domain. Active Directory provides MFA (Multifactor authentication.) User Identity Management. Device Registration, Password Management, Monitoring, Auditing and Alerting. • Assign USB Mass storage device Block policy for all computers
• Installing Cisco PIX Firewall
• Creating VLAN for Limit the size of broadcast domains and Improves network performance • Every and each branch will be monitored by 24 hours CCTV surveillance • Properly enforce data privacy regulations throughout Europe country (European Data
Protection Regulation). The GDPR system was a resounding success as a model for breach notification policy
